Online Technical Training Blog
PLC's and SCADA: Vulnerabilities and Security Issues
Programmable Logic Controllers (PLCs) are used in almost all industrial processes and are an integral part of a nations industry and manufacturing infrastructure. Power grids, water treatment plants and traffic lights are just a few of the parts of infrastructure that are controlled by PLCs. To monitor these systems a Supervisory Control and Data Acquisition (SCADA) interface is used. SCADA systems “are highly distributed systems used to control geographically dispersed assets, often scattered over thousands of square kilometers, where centralized data acquisition and control are critical to system operation.” (EEP.com) As critical as these systems are for a functioning society, it is assumed that security is a top priority. Unfortunately, SCADA systems have many vulnerabilities. Research from the Ponemon Institute stated that “70 percent of companies responsible for world's water, power and other critical functions reported at least one security breach that led to the loss of confidential info or disruption operations in the last 12 months.”(scmagazine) Stuxnet was a high-profile SCADA attack that targeted PLCs in Iran’s nuclear program. Developed by the United States and Israel, Stuxnet is regarded as the worlds first cyber weapon, which spread as quickly as it did with the help of SCADA security issues.
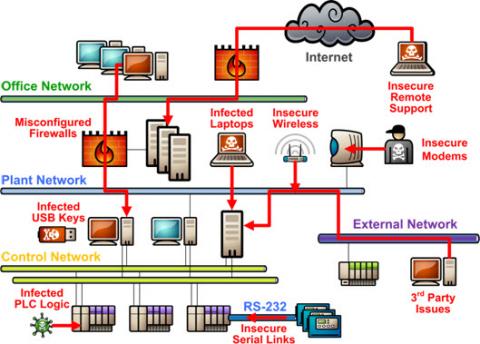
GBC’s PLC II program delves into many of SCADA’s security vulnerabilities, of which one is human error. Inadvertent mistakes, disgruntled employees, laptops with viruses, and other human-related conditions all present a major threat to the safe and secure operation of a SCADA system. An example of this occurred in January 2014. A disgruntled employee in Maryland hacked into a SCADA controlled sewage treatment plant and released millions of gallons of raw sewage into the ocean. The employee was apprehended by the authorities but the environmental damage had been done. Another security vulnerability in SCADA systems are inadvertent connections to the internet. “SCADA systems may not be directly connected to the internet, they are almost always connected to an internal network that has direct internet access.” (scmagazine) Furthermore, in the past certain sensors and monitoring devices communicated using their own specific programming language. Currently, these sensors are now increasingly using TCP/IP language. This allows sensors to communicate with Windows-powered machines that engineers are using to monitor and control systems. Almost all modern SCADA systems are not closed systems, and at some point there is a connection to a corporate network or other third-party which increases their exposure to attacks from external sources.
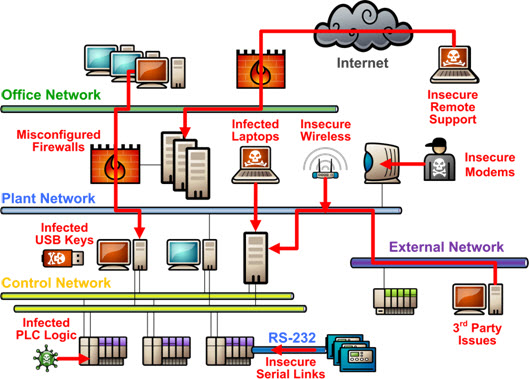 |
| Source: Tofino Security |
These vulnerabilities are what allowed the Stuxnet virus to propagate so quickly. The creators of Stuxnet first infected four companies that are related to Iran’s nuclear program. One of these companies had installed Siemens S7-400 PLCs which were designed to control Iran’s centrifuges used to enrich uranium. Stuxnet’s primary method of infecting machines was through USB drives. Workers at these four companies then inadvertently transferred files from their company’s headquarters to Iran’s nuclear facility via the infected USB sticks. At this point Stuxnet used SCADA to infect Siemens PLC’s. Specifically, Stuxnet hacked into files and added malicious code that can access, read, write, and delete code blocks on the PLC. Since the PLC’s controlled centrifuges, this malicious code caused the centrifuges to spin out of control and self-destruct.
This attack was targeted at Iran, however, Stuxnet has spread well-beyond its initial target. It is reported that in 2010 Chevron had its network infected with Stuxnet. The Wall Street Journal mentioned “Chevron found the virus in its systems after the malware's existence was first reported in a blog post in July 2010, according to Mark Koelmel, general manager of the earth-sciences department at the big U.S. oil company.” (WSJ)
SCADA vulnerabilities have played a role in the uncontrolled spread of Stuxnet and security still does not remain a top priority for SCADA users. When the Ponemon institute asked SCADA users about priority “Only 28 percent said that security was ranked as a top five strategic priority for their organization, and yet minimizing downtime was a top priority for the majority of respondents.” (scmagazine)


